Cloud Detection and Response solution for AWS
Cloud Detection and Response solution for AWS
Detect when your AWS environment is under attack
Vectra AI's Attack Signal Intelligence™ puts the power of AI at your fingertips to stop AWS attacks in real time — long before a breach occurs.

Find attackers in your AWS environment
With 11 references in the MITRE D3FEND framework — more than any other vendor — only Vectra AI provides Cloud Detection and Response (CDR) powerful enough to reveal the earliest signs of hybrid cloud compromise.
#1
Most-referenced in MITRE D3FEND
35
AI threat detection patents
>90%
MITRE ATT&CK coverage
Our customers
Detect the attacks even native AWS solutions miss
When The Hyde Group needed critical visibility into threat behaviors within their AWS environment, they turned to Vectra AI.
"We have some native AWS tools running but they don't compare to Vectra AI."

Information Technology Security Manager, The Hyde Group
CDR Differentiators
Only Vectra CDR for AWS provides
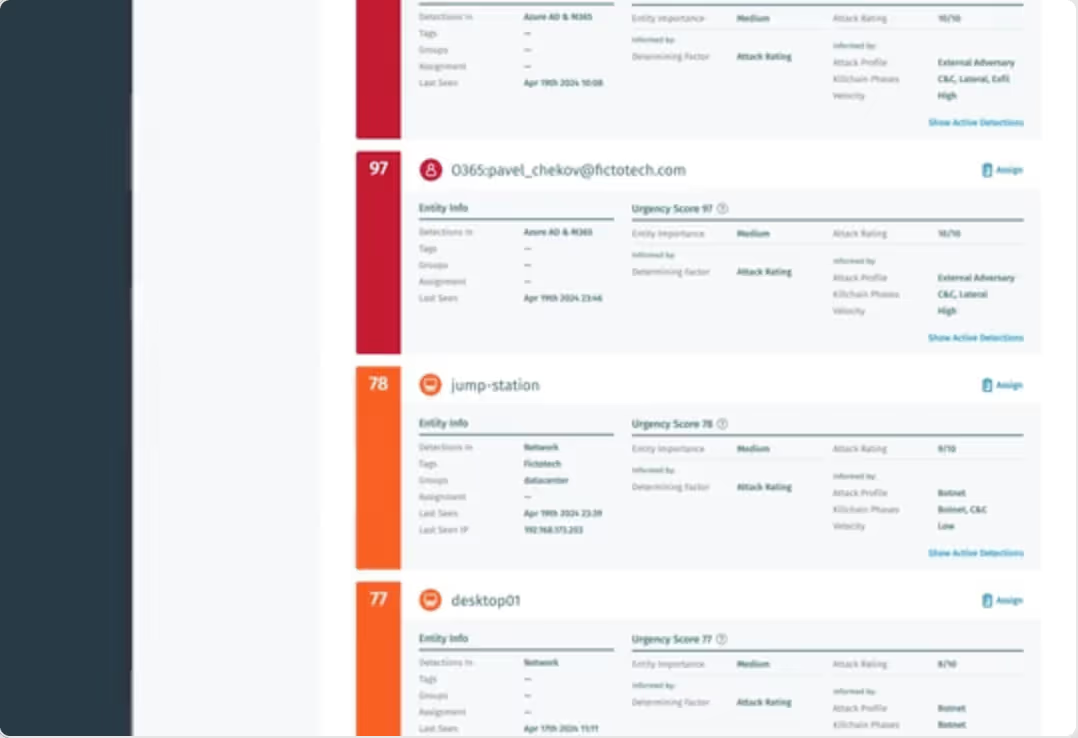
Find real attacks as they progress in your AWS environment in real-time with Attack Signal Intelligence, the industry’s most advanced AI focusing on tactics bad actors use to hide.
Explore our AI
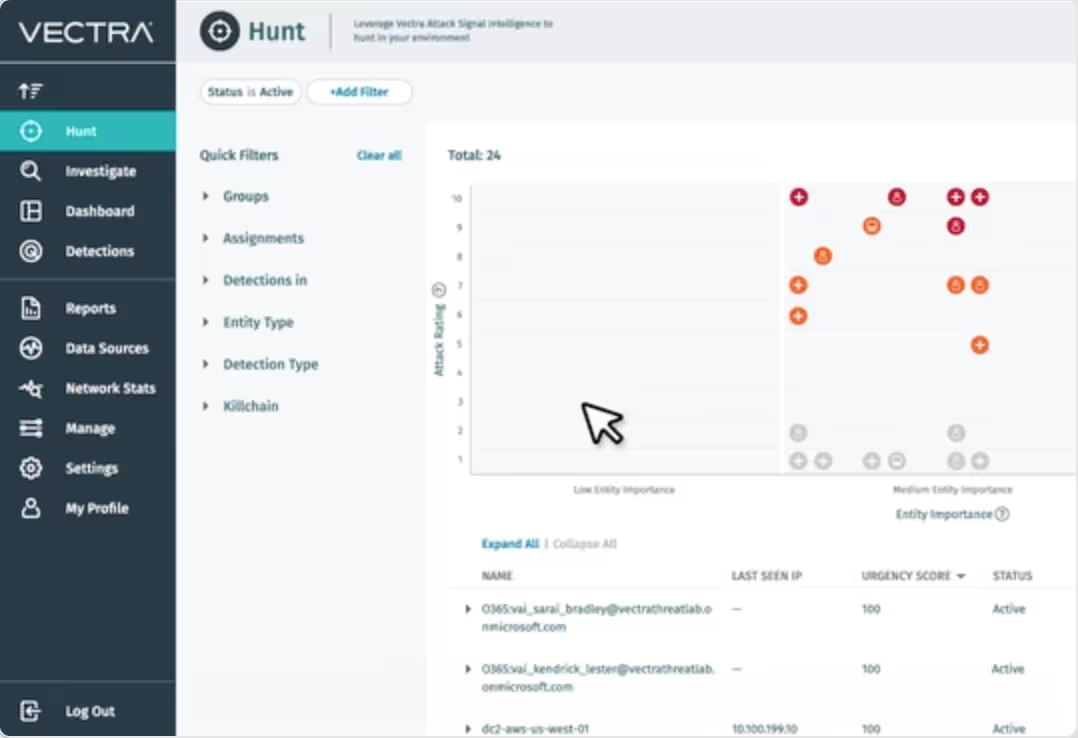
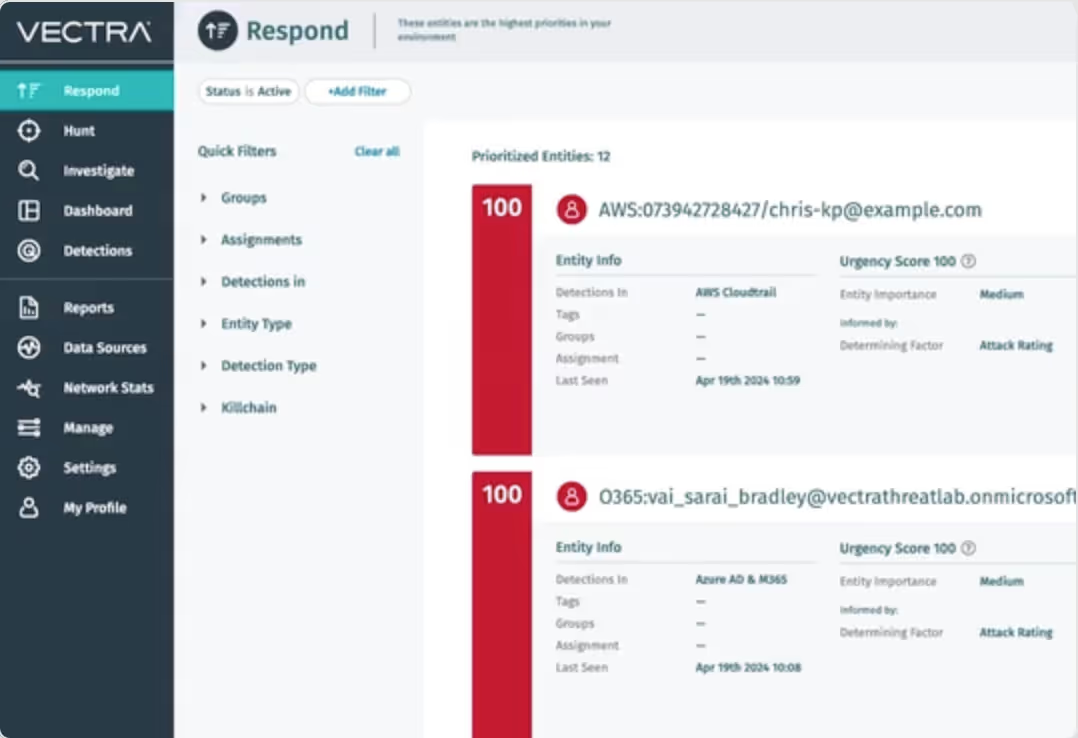
Respond to incidents in real-time with intelligence that gives you the complete picture on account misuse and TTPs across your entire AWS estate.
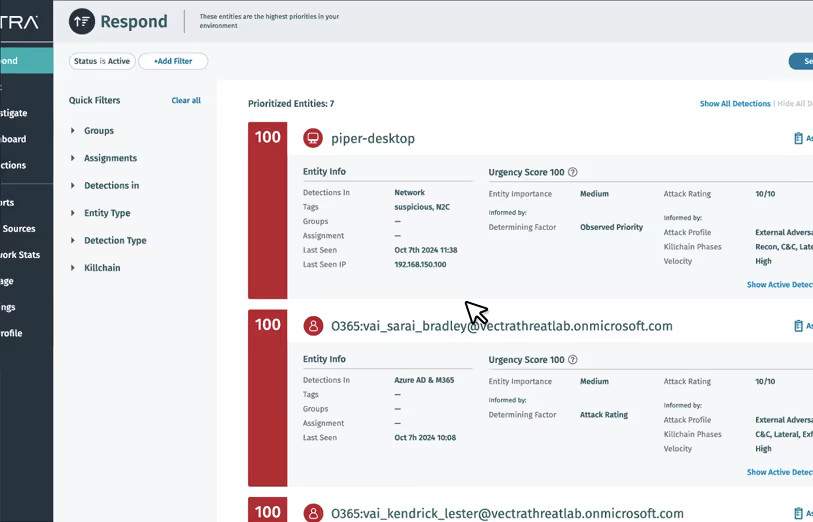
Put contextualized threat activity at SOC analysts’ fingertips for faster, more accurate threat hunting and response.

Extend your team with skilled Vectra MDR analyst reinforcements committed to co-defending your AWS infrastructure.
Explore our AI

AI-driven Attack Signal Intelligence
Find real attacks as they progress in your AWS environment in real-time with Attack Signal Intelligence, the industry’s most advanced AI focusing on tactics bad actors use to hide.
Explore our AI

Complete visibility and context
Respond to incidents in real-time with intelligence that gives you the complete picture on account misuse and TTPs across your entire AWS estate.

Put contextualized threat activity at SOC analysts’ fingertips for faster, more accurate threat hunting and response.

Continued AWS support for 24x7x365 coverage
Extend your team with skilled Vectra MDR analyst reinforcements committed to co-defending your AWS infrastructure.
Explore Vectra MDR
CDR Capabilities
With Vectra CDR for AWS, detect and disarm attacks in minutes — no matter where they occur
AI-driven Detection
Expose the complete narrative of an attack and cover over 90% MITRE ATT&CK techniques.
AI-driven Triage
Reduce alert noise by 80% or more with ML that understands your environment.
AI-driven Prioritization
Harness security AI to automate prioritization to escalate the threats that matter most to the business.
Instant Investigations
Streamline research of Azure AD, M365 and AWS Control Plane logs to understand the attacks facing you in minutes.
Ecosystem Integrations
Integrate existing tech for correlation and context and to automate analyst workflows and response controls.
Account Lockdown
Stay in control of your AWS accounts without having to default to an all-or-nothing account lockdown approach.
Ecosystem
The most advanced AWS threat detection solution
Enterprises worldwide rely on Vectra’s deep integration with AWS to find and stop real attacks.
- Enrich Amazon Security Lake with Attack Signal Intelligence
- Complement Amazon GuardDuty with more coverage and context
- See the earliest signs of an attack targeting IaaS and PaaS
Self-Guided Tours
Experience the power of the Vectra AI Platform
Click through at your own pace to see what analysts can achieve in a platform powered by the world's most accurate attack signal.

Resources
