Maze ransomware, originally known as "ChaCha ransomware," was first discovered on May 29, 2019, by Jerome Segura. Maze quickly gained notoriety for its innovative approach to ransomware attacks, combining data encryption with data theft, a tactic that became known as double extortion. Attackers not only encrypted data but also stole it, threatening to publicly release the stolen information if the ransom was not paid.
Although Maze announced its retirement in late 2020, the threat landscape continues to be influenced by the techniques it pioneered. In fact, in June 2020, the criminals behind Maze teamed up with two other ransomware groups: LockBit and RagnarLocker. This collaboration among ransomware groups was a significant development, as it demonstrated how different threat actors are coordinating to amplify their impact. This evolution underscores the importance of continuously improving detection and mitigation strategies.
For more detailed information on LockBit ransomware, visit our LockBit page to learn how Vectra AI helps detect and respond to these threats.
How does Maze Ransomware works?
Maze operates like many other ransomware families but takes it a step further by using double extortion. In addition to encrypting data, Maze exfiltrates sensitive information to servers controlled by the attackers. If victims do not pay the ransom, the attackers threaten to leak the stolen data. This model has been adopted by other prominent ransomware groups, such as REvil (Sodinokibi) and Clop, which have refined these tactics for maximum leverage.
Maze, LockBit, and RagnarLocker rely on sophisticated techniques, including encrypted command and control (C2) channels, deception, and the use of native Windows functions to evade detection by traditional security tools. Vectra AI's behavior-based models detect these threats consistently because they focus on attacker behaviors, not static signatures. While attacker infrastructure and tools may change, their behaviors—such as reconnaissance, lateral movement, and data exfiltration—remain more stable, allowing Vectra to detect both Maze and other evolving ransomware threats.
How does a modern Ransomware attack looks like?
Let’s start by looking at a common timeline of a modern ransomware attack:
- Organization is compromised via spear phishing email
- C2 is established
- Executable is dropped and threat actor has long lead time where credential theft and other localized reconnaissance occurs
- Additional tools are downloaded to host such as psexec, Cobaltstrike, Empire, ADFind
- Recon tools executed and results collected
- Threat actor copies payloads to targets in the environment
- Processes are stopped as defensive evasion and encryption takes place
- Ransom note dropped
- Data exfiltration via C2 or TOR
From a SOC perspective, let’s simplify this and distill it into five observable steps.
- Attacker gains a foothold in the targeted company
- Attacker performs reconnaissance in order to find information of interest, or passwords that may enable lateral movement in the network or privilege escalation
- Lateral movement in order to control most hosts
- Exfiltration of sensitive data
- Finally, deployment and execution of Maze ransomware toward the previously created channels
Note that those steps may or may not be present, depending of the actor. As the techniques varies, potential detections listed below cannot be considered certain. Note as well that some people can just open a sample of Maze by accident, infect themselves, which would only trigger ransomware detection, as no interaction within a C2 channel will be performed.
How Can Vectra AI Detect Maze and Its Variants?
Vectra detects active Maze ransomware infections, as well as newer variants like LockBit and RagnarLocker. Before ransomware encrypts data, it must first perform internal reconnaissance to locate sensitive files and network shares. This behavior is detected by Vectra's AI-driven threat models, which triage all behaviors associated with compromised hosts.
Critical risks, such as ransomware infections, are assigned the highest threat and certainty scores, prioritizing them for immediate investigation by SOC teams. What’s more, Vectra customers had this detection capability in place before Maze and its variants struck, showcasing the advantage of proactive threat detection.
Maze Attack Progression: What to Expect
Let’s take a closer look at a common ransomware attack timeline, using Maze as a model:

Step 1 - Initial compromise
For initial compromise, some campaigns start with malicious documents, used to launch a cobalt strike instance in order to gain remote control of the “patient zero”. Several cases reported came from a direct compromising, by the actor, using stolen credentials, exploitation of vulnerable software, or weak password on Internet facing devices. The most observed tool used to take control of the patient zero appears to be CobaltStrike.
Step 2 - Recon and privilege escalation
Actors sometimes used privilege escalation in order to be able to execute and deploy the ransomware, move laterally, or discover interesting files. This attack step comprises the reconnaissance behavior.
- This can be done using mimikatz locally.
- The actor can look for files with the word “password” in it, which may trigger file share enumeration.
- Some usage of the enumeration/reconnaissance feature of BloodHound tool have been reported, for the attacker to find hosts of interest, and better understand the target’s architecture.
- Many different tools have been reported for the reconnaissance stage, but they all have the same objective, understand network architecture, places they can move, where to find accounts that may help move further….
- All these behaviors could trigger our recon detections, such as port scan, internal darknet scan, suspicious LDAP query, File share enumeration and so on - you can access the full list of our detections here.
Once the attacker gets a foothold in the target’s environment, several reconnaissance attempts, as well as lateral movement are performed towards other targets.
The screenshot below clearly shows this behavior, IP – 10.50.2.103 being the principal entry point, showing lateral movement and significant reconnaissance behavior.

Step 3 - Lateral movement
For lateral movement itself, attackers mostly leverage Cobalt strike from their initial foothold.
- Some actors create themselves an account on the infected domain. This action could create privilege access anomalies, such as Privilege Anomaly: Unusual Account on Host
- In case exploitation such as psexec is performed in order to move laterally using the tool, Suspicious Remote Execution is susceptible to fire.
- Some actors used RDP, in this case, Suspicious RDP and RDP Recon detection are susceptible to trigger. One actor has been reported using a tunnel for RDP, which may show as Suspicious Relay, depending on method used by the attacker.
In the Suspicious Remote Execution detail, we see the attacker operating psexec to manage services in neighboring hosts.

Step 4 - Exfiltration
Finally, several cases show exfiltration attempts, prior to encryption by maze, which are done in various manners, mostly towards ftp or cloud hosting services.
- Depending of the volume of exfiltrated files, Data smuggler and Smash and Grab could trigger
- In case the attacker decides to exfiltrate data from a SharePoint site, we can expect “Unusual volume” O365 detection ;)

Note here that prior to the detonation of the ransomware itself, the host pc4 suffered external remote access and Smash andGrab exfiltration attempts, which is here part of the exploit chain.
The external remote access is always a strong indicator of an external adversary when combined with reconnaissance detections. In detection detail here you find the type of C2 application, in this case Teamviewer. C2 alerts should always be investigated to rule out threats. Do not rely solely on threat intel but consider the broader scope of activity. Ask yourself:
- Is the host also performing recon?
- Is there suspicious account activity on the host?
- Is the destination logical (in this case an IP in Netherlands)?
- Did endpoint detection and response (EDR) trigger any alerts?

Step 5 - Ransomware
Maze ransomware is then deployed via channels. This one obviously triggers ransomware file activity, as shown below.
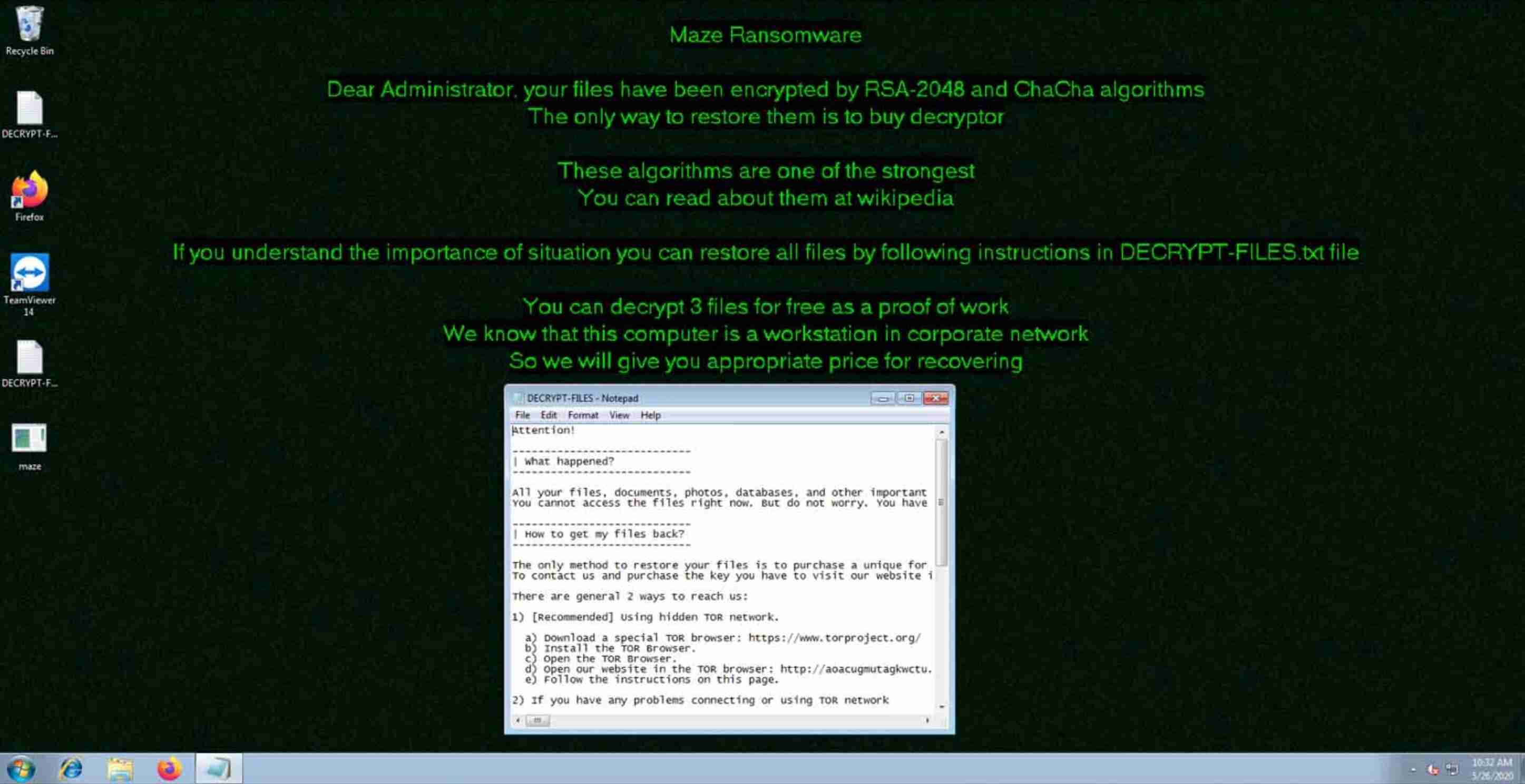
Regarding Ransomware detection itself, the detection view shows the number of files affected, as well as shares names. The ransomware note is also given, as it can help identify certain families of malware by its name:


Using Recall enhanced view, we can see clearly that at the time of the attack, some external sessions were launched:


Post Incident Report: 5 Steps to identify an Actual Maze Ransomware attack
Below is a summary of an actual post incident report that shows the steps taken to identify the early indicators of a ransomware attack and prevent the encryption of network file shares.
Vectra has been authorized to publish this post-incident report by ensuring anonymity and protecting the customer’s private data. This type of report is ordinarily kept confidential for internal analysis only.
- Inside the compromised network on Day 1—one week prior to the intended ransomware detonation—the Vectra Consulting Analyst Team detected unmistakable reconnaissance and lateral movement attack behaviors. These phases of the attack lifecycle indicated the attacker was looking for critical systems to compromise before encrypting network file shares for ransom.
- Vectra showed that scans came from a wide range of hosts and other scans were related to ransomware activities as network file shares were enumerated.
- Uncovering additional evidence, Vectra observed that one compromised host was communicating with a known malicious IP address in Ukraine that has been associated with Sodinokibi malware.
- External connections were performed successfully to a Ukraine IP address with a data transfer of about 80 MB.
- The number of detections identified by Vectra was concerning due to the sheer volume of data that was being sent to the outside.
Additional information from the customer linked the attack to Maze ransomware.
Check out this post-incident report which shows the importance of early cyberattack detection to avert damage and catastrophic data breaches. With certainty and precision, it is vital to identify precursor threat behaviors, swiftly investigate incidents, and arm yourself with the appropriate response tools.
Detect and stop ransomware with Vectra AI
Ransomware, especially the kind pioneered by Maze, is evolving. Threat actor groups are not only advancing their tactics but also teaming up, as we’ve seen with Maze’s collaboration with LockBit and RagnarLocker. This means the stakes are higher than ever for organizations that need to defend their critical infrastructure.
To stay ahead of these threats, Vectra AI leverages AI-powered behavioral analytics to detect sophisticated ransomware groups and Advanced Persistent Threat (APT) actors.
For more information on how cybercriminals operates and how Vectra AI can protect your environment, check out our threat briefings and threat actors pages.
To get in touch with our experts, our newly announced Vectra services enable our customers to mature their security operations and empower them with access to the people at Vectra who are most knowledgeable. And as always, don’t hesitate to contact us to learn more or schedule a demo.

