Server-Side Request Forgery (SSRF): Complete Security Guide for 2025
Key insights
- SSRF attacks surged 452% in 2024 driven by AI-powered automation tools, with organizations facing 4-8 week recovery periods from successful breaches
- Oracle EBS CVE-2025-61882 demonstrates active exploitation of SSRF for remote code execution, prompting CISA's urgent October 27, 2025 patch deadline
- Cloud metadata services at addresses like 169.254.169.254 remain primary targets for credential theft and infrastructure compromise
- Effective SSRF defense requires layered controls combining input validation, network segmentation, and behavioral analysis rather than signature-based detection
In October 2025, the cybersecurity world witnessed a watershed moment when the Cl0p ransomware group successfully weaponized a critical SSRF vulnerability in Oracle E-Business Suite, affecting Fortune 500 organizations globally. According to CrowdStrike's threat intelligence, this campaign marked a tactical evolution in how sophisticated threat actors leverage server-side request forgery attacks. The 452% surge in SSRF attacks between 2023 and 2024 isn't just another statistic — it represents a fundamental shift in the attack landscape, driven by AI-powered automation tools that have democratized what was once the domain of elite hackers.
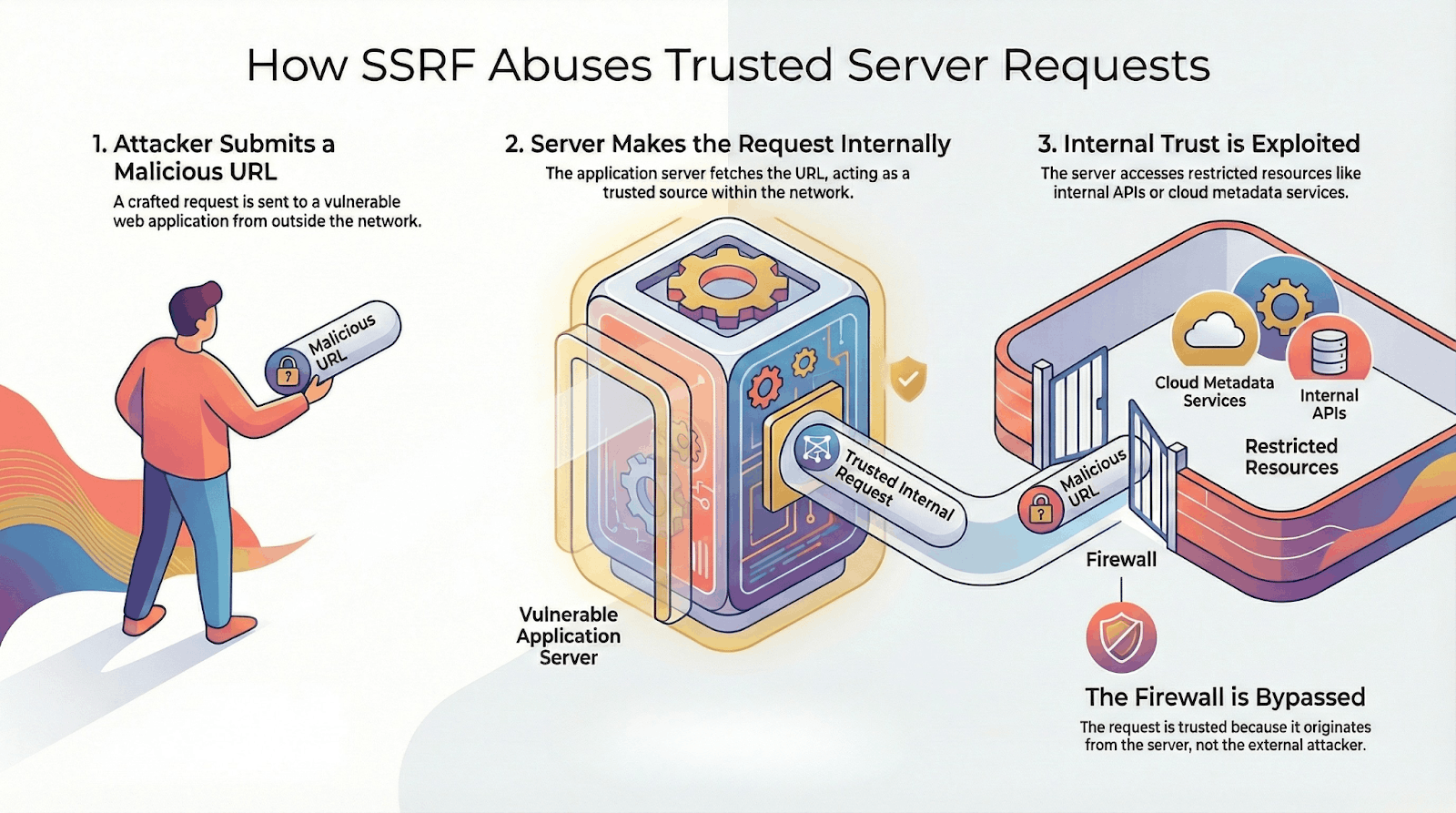
At its core, SSRF exploits trust relationships between application servers and internal systems. Because the forged request originates from a trusted server, internal services treat it as legitimate, even when the destination was attacker-controlled. This is how SSRF bypasses network segmentation and perimeter-based controls that would normally block external access.
What is server-side request forgery (SSRF)?
Server-side request forgery (SSRF) is a web security vulnerability that enables attackers to manipulate a server into making unauthorized requests to internal systems, cloud metadata services, or external resources on their behalf. By exploiting trust relationships between servers, SSRF attacks bypass network security controls, access restricted resources, and potentially achieve remote code execution through chained exploits. This vulnerability transforms legitimate server functionality into a powerful attack proxy.
The fundamental danger of SSRF lies in its ability to abuse the implicit trust that internal systems place in application servers. When a vulnerable application accepts user-controlled URLs without proper validation, attackers can redirect the server's requests to unintended destinations. This breach of trust becomes particularly devastating in cloud environments, where metadata services provide credentials and configuration data accessible only from within the infrastructure.
SSRF's inclusion as number 10 in the OWASP Top 10 2021 reflects its growing prevalence and impact. The vulnerability ranked first in the OWASP community survey that led to its addition, highlighting the security community's recognition of SSRF as a critical threat. Modern applications' reliance on microservices, APIs, and cloud services has exponentially increased the attack surface for SSRF exploitation.
Breaking news: Oracle EBS and AI-powered SSRF surge
The cybersecurity landscape shifted dramatically in October 2025 with the disclosure of CVE-2025-61882, a critical SSRF vulnerability in Oracle E-Business Suite versions 12.2.3 through 12.2.14. CrowdStrike's analysis reveals that the Cl0p ransomware group, tracked as Graceful Spider, had been exploiting this zero-day since August 2025. The vulnerability, scoring 9.8 on the CVSS scale, allows pre-authenticated attackers to chain SSRF with CRLF injection, authentication bypass, and unsafe XSLT processing to achieve remote code execution.
CISA's addition of this vulnerability to the Known Exploited Vulnerabilities catalog on October 6, 2025, mandates federal agencies patch by October 27, 2025. This designation indicates confirmed exploitation against U.S. government systems and critical infrastructure, elevating the urgency beyond typical vulnerability disclosures.
Compounding this crisis, SonicWall's 2025 Cyber Threat Report documents a staggering 452% increase in SSRF attacks from 2023 to 2024. This surge correlates directly with the proliferation of AI-powered exploitation tools that automatically identify vulnerable endpoints, generate context-aware bypass payloads, and evade traditional security controls. These tools have effectively lowered the barrier to entry, enabling less-skilled threat actors to execute sophisticated SSRF campaigns previously requiring deep technical expertise.
For security professionals managing increasingly complex cloud infrastructures, understanding SSRF has become non-negotiable. These vulnerabilities don't just expose internal resources; they provide attackers with the keys to your cloud kingdom, turning trusted servers into malicious proxies that bypass traditional security controls. As organizations race to patch Oracle EBS before CISA's October 27, 2025 deadline, the broader question looms: How did SSRF become the attack vector of choice, and what can modern security teams do to defend against it?
How SSRF attacks work
SSRF attacks exploit the fundamental architecture of modern web applications where servers routinely fetch resources from URLs. Attackers manipulate these legitimate functions by injecting malicious URLs that redirect the server's requests to unintended targets. The attack succeeds because the request originates from the trusted application server, bypassing firewall rules and network segmentation that would block direct external access.
The exploitation process begins when an attacker identifies functionality that accepts URL input — common examples include webhook implementations, PDF generators, image processing features, and API integrations. Through careful manipulation of URL parameters, attackers can force the server to access internal resources, cloud metadata endpoints, or even perform port scanning of the internal network. Network detection and response systems increasingly focus on identifying these anomalous server-initiated connections as traditional perimeter defenses prove inadequate.
Consider a vulnerable image processing service that accepts user-supplied URLs to fetch and resize images. An attacker might submit http://169.254.169.254/latest/meta-data/iam/security-credentials/ instead of a legitimate image URL. The server, running on AWS EC2, would dutifully fetch this internal metadata endpoint, potentially exposing IAM credentials that grant access to the entire AWS account. This simple example demonstrates how SSRF transforms innocuous functionality into a critical security breach.
Protocol handlers extend SSRF's reach beyond HTTP requests. Vulnerable applications may support protocols like file:// for local file access, gopher:// for arbitrary TCP connections, dict:// for dictionary server queries, or ftp:// for FTP connections. Each protocol opens unique exploitation paths — file:///etc/passwd might expose system users, while gopher:// can craft requests to internal services like Redis or Memcached. Modern applications increasingly restrict these protocols, but legacy systems and misconfigured services remain vulnerable.
Common SSRF attack patterns
SSRF attacks follow predictable patterns that security teams must recognize. The most straightforward pattern targets the vulnerable server itself, attempting to access local resources through localhost references like http://127.0.0.1/admin or http://localhost:8080/metrics. These attacks exploit services bound to the loopback interface, assuming they're protected from external access.
Backend system exploitation represents a more sophisticated pattern where attackers target internal infrastructure invisible from the internet. By crafting requests to RFC1918 addresses like http://192.168.1.10/api/internal, attackers can interact with databases, internal APIs, or administrative interfaces. The March 2025 coordinated campaign involving over 400 IPs demonstrated this pattern at scale, simultaneously targeting multiple internal services across victim organizations.
Blind SSRF attacks present unique challenges because the attacker doesn't receive direct responses from their forged requests. Instead, they must infer success through timing analysis, error messages, or out-of-band interactions. DNS rebinding attacks exemplify advanced blind SSRF techniques, where attackers control a domain that initially resolves to a legitimate IP, then changes to an internal address after passing validation checks. These time-of-check to time-of-use (TOCTOU) vulnerabilities bypass even well-implemented URL filters.
In blind SSRF scenarios, attackers infer success indirectly through timing differences, DNS callbacks, or side effects, rather than direct responses, making these attacks harder to detect and easier to overlook during testing.
SSRF bypass techniques and evasion
Security controls designed to prevent SSRF often fail because attackers exploit gaps between URL validation logic and how requests are ultimately resolved and executed. Many defenses rely on superficial string matching rather than understanding how URLs are parsed, normalized, and resolved at runtime.
Common SSRF bypass techniques include:
- Encoded or obfuscated internal IP addresses
- Alternative IP formats (decimal, hexadecimal, or octal)
- DNS rebinding and delayed resolution
- URL parser differentials between validation and execution
Simple evasion techniques include URL encoding, where attackers disguise internal addresses using encoded values. For example, %31%32%37%2e%30%2e%30%2e%31 decodes to 127.0.0.1, allowing attackers to bypass basic blacklist filters. Multiple encoding layers, URL, Unicode, or HTML, are often combined to evade detection.
Attackers also exploit alternative IP address representations. Cloud metadata endpoints such as 169.254.169.254 can be expressed in decimal (2852039166), hexadecimal (0xA9FEA9FE), or octal formats. Applications that fail to normalize IP input correctly may allow access to restricted internal services even when standard dotted notation is blocked. DNS rebinding further complicates detection by resolving a domain to a benign address during validation and switching to an internal address at execution time.
More advanced bypasses target parser differentials, inconsistencies between how URLs are interpreted during validation versus request execution. For example, http://expected-host@evil-host/ may pass validation if the application extracts expected-host, while the actual request is sent to evil-host. Similar issues arise with fragments (#) or malformed authority components. These discrepancies explain why allowlisting known-safe destinations and enforcing consistent URL parsing are far more effective than blacklist-based SSRF defenses.
How SSRF leads to remote code execution (RCE)
SSRF is rarely the final objective. In many real-world incidents, it serves as an entry point for deeper compromise.
Common escalation paths include:
- Accessing cloud metadata services to steal credentials
- Interacting with internal APIs, databases, or admin panels
- Chaining SSRF with deserialization flaws, command injection, or misconfigured services
When attackers gain authenticated access to internal systems through SSRF, remote code execution becomes a realistic outcome rather than a theoretical risk.
Types of SSRF attacks
SSRF vulnerabilities manifest in various forms, each presenting unique exploitation opportunities and defensive challenges. Understanding these categories helps security teams implement targeted controls and recognize attack patterns in their environments.
Basic SSRF attacks target the vulnerable server directly, exploiting services available on localhost or the loopback interface. These attacks succeed because many applications bind administrative interfaces, debugging endpoints, or metrics collectors to 127.0.0.1, assuming this provides adequate isolation. An attacker might access http://localhost:8080/actuator/health to gather application intelligence or http://127.0.0.1:6379/ to interact with an unprotected Redis instance. While seemingly simple, these attacks can expose sensitive configuration data, application secrets, or provide footholds for further exploitation.
Backend SSRF attacks leverage the vulnerable server's network position to access internal systems. This category proves particularly damaging in modern architectures where microservices communicate over private networks. Attackers craft requests targeting internal IP ranges, accessing databases, message queues, or administrative panels that lack authentication due to their presumed isolation. The Capital One breach of 2019, detailed in this comprehensive analysis, exemplified this pattern when SSRF enabled access to internal AWS resources, ultimately exposing data of over 100 million individuals.
Blind SSRF presents unique challenges as attackers receive no direct response from their forged requests. Detection requires out-of-band techniques like DNS lookups to attacker-controlled domains, timing-based inference, or triggering observable side effects. Security teams often overlook blind SSRF during testing, yet these vulnerabilities can enable data exfiltration through DNS tunneling or interaction with internal services that modify application state. Modern exploitation frameworks automate blind SSRF detection through sophisticated callback mechanisms and timing analysis.
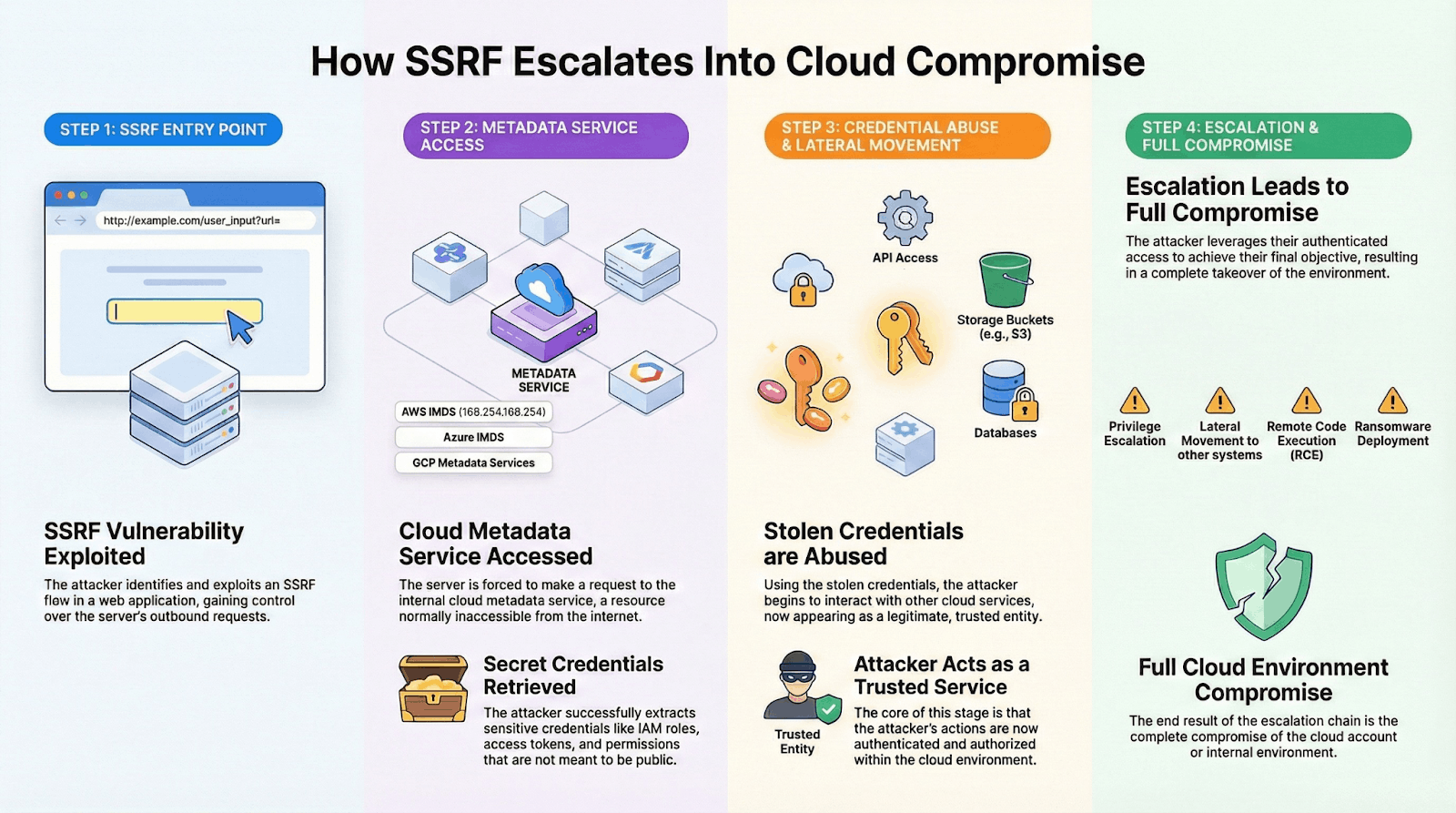
Cloud metadata exploitation
Cloud metadata services represent the crown jewels for SSRF attackers. These services, accessible at predictable addresses like 169.254.169.254 for AWS or metadata.google.internal for GCP, provide instance configuration, credentials, and secrets to cloud workloads. Cloud control plane protection strategies must account for SSRF as a primary vector for metadata compromise.
The Azure OpenAI SSRF vulnerability (CVE-2025-53767), scoring a perfect CVSS 10.0, demonstrated the catastrophic potential of metadata service exploitation. Insufficient input validation in user-supplied URLs allowed attackers to retrieve Azure managed identity tokens, enabling lateral movement across tenant boundaries. Microsoft's patch addressed the immediate vulnerability, but the incident highlighted systemic risks in cloud service architectures.
AWS's Instance Metadata Service (IMDS) evolution from v1 to v2 directly responds to SSRF threats. IMDSv1's simple HTTP GET requests made it trivial for SSRF attacks to retrieve credentials. IMDSv2 introduced session-based authentication requiring PUT requests with custom headers — defenses specifically designed to thwart SSRF exploitation. Despite AWS's strong recommendations, many organizations haven't migrated to IMDSv2, leaving their infrastructure vulnerable to credential theft through SSRF.
Application-specific SSRF variants
Modern application architectures introduce novel SSRF variants that extend beyond traditional web applications. Serverless functions, particularly those processing user-supplied URLs for webhooks or data ingestion, create ephemeral but powerful SSRF opportunities. These functions often have broad IAM permissions and network access, making them attractive targets for metadata service attacks.
GraphQL implementations deserve special attention as their query complexity can mask SSRF vulnerabilities. Nested queries and field resolvers that fetch remote resources based on user input create multiple SSRF vectors within a single endpoint. The flexibility that makes GraphQL powerful also complicates input validation, as malicious URLs might be deeply nested within complex query structures.
Container orchestration platforms like Kubernetes introduce their own SSRF risks through service discovery mechanisms and API servers. An SSRF vulnerability in a pod can expose the Kubernetes API, service account tokens, or cluster secrets. The blast radius expands dramatically when SSRF enables access to container registries, CI/CD pipelines, or infrastructure automation tools that trust internal network origins.
SSRF vs CSRF: What’s the difference?
SSRF and CSRF are often confused because both exploit trust relationships, but they target different components of an application.
- SSRF forces a server to make unauthorized requests to internal or external systems.
- CSRF tricks a user’s browser into sending unintended requests to a trusted application.
In practice, SSRF is an infrastructure-level risk that can expose cloud credentials or internal services, while CSRF primarily affects user actions and session integrity. Both require different detection and prevention strategies.
SSRF in cloud environments
Cloud environments amplify SSRF risks through their reliance on metadata services, managed identities, and API-driven architectures. The shift from traditional network perimeters to identity-based security models means that SSRF vulnerabilities can directly lead to privilege escalation and account takeover.
The shared responsibility model complicates SSRF prevention in cloud deployments. While cloud providers secure the underlying infrastructure and metadata service endpoints, customers must properly configure their applications, implement network controls, and manage identity permissions. This division of responsibility creates gaps that sophisticated attackers exploit through SSRF attacks. Organizations often assume cloud provider security controls are sufficient, overlooking application-layer vulnerabilities that bypass these protections.
Multi-cloud strategies introduce additional complexity as each provider implements metadata services differently. AWS uses 169.254.169.254 with optional IMDSv2 protections, Azure employs 169.254.169.254 with required headers, and GCP uses metadata.google.internal with project-specific endpoints. Security teams must understand these variations to implement effective controls across heterogeneous cloud environments. Cloud detection and response for AWS platforms increasingly incorporate SSRF-specific detection logic tailored to each cloud provider's architecture.
AWS metadata security
AWS metadata security centers on the Instance Metadata Service (IMDS), which provides critical instance information and temporary credentials to EC2 instances. The AWS documentation details two versions: IMDSv1 (request/response) and IMDSv2 (session-oriented). IMDSv1's simplicity makes it vulnerable to SSRF attacks — a simple GET request to http://169.254.169.254/latest/meta-data/ returns instance metadata without authentication.
IMDSv2 implements multiple defensive layers specifically designed to thwart SSRF attacks. Session initialization requires a PUT request with a specific header, returning a session token valid for six hours. Subsequent metadata requests must include this token as a header, preventing simple SSRF vulnerabilities from accessing metadata. The Time-To-Live (TTL) header set to 1 ensures tokens can't traverse network boundaries, adding another protection layer.
Despite these improvements, organizations face operational challenges migrating to IMDSv2. Legacy applications may break, third-party software might require updates, and automation scripts need modification. AWS provides migration tools and compatibility analyzers, but the transition requires careful planning and testing. Security teams must balance the urgent need for SSRF protection against operational stability, often implementing compensating controls during the migration period.
Azure and GCP considerations
Azure's approach to metadata security differs from AWS, implementing mandatory header requirements from the outset. The Azure Instance Metadata Service (IMDS) requires the Metadata: true header for all requests, providing baseline SSRF protection. However, sophisticated SSRF vulnerabilities that allow header injection can still bypass this control, as demonstrated by the Azure OpenAI incident.
Azure Managed Identities add another dimension to SSRF risks. These identities, assigned to resources like virtual machines or App Services, can access Azure resources without storing credentials. An SSRF vulnerability in an application with a managed identity can lead to unauthorized access to databases, storage accounts, or key vaults. The blast radius depends on the identity's assigned permissions, highlighting the importance of least-privilege access controls.
Google Cloud Platform implements unique metadata service protections while maintaining different endpoint structures. GCP requires the Metadata-Flavor: Google header and uses the metadata.google.internal domain rather than IP addresses. This domain-based approach complicates some SSRF attacks but doesn't eliminate the risk. GCP's project-specific metadata endpoints and service account scoping provide additional isolation, but SSRF vulnerabilities can still expose sensitive project metadata and service account tokens.
Detecting and preventing SSRF attacks
Effective SSRF defense requires a multi-layered approach combining preventive controls, detection mechanisms, and incident response capabilities. Organizations must move beyond simple input validation to implement comprehensive security strategies that address SSRF throughout the application lifecycle.
Prevention starts with secure coding practices that treat all user-supplied URLs as potentially malicious. Input validation should use strict allowlists rather than blacklists, explicitly defining acceptable protocols, domains, and ports. URL parsing must occur consistently across validation and execution contexts to prevent parser differential attacks. The OWASP SSRF Prevention Cheat Sheet provides comprehensive guidance on implementing these controls effectively.
Network segmentation provides crucial defense-in-depth against SSRF attacks. Applications that fetch external resources should operate in isolated network zones with restricted access to internal services. Egress filtering blocks unauthorized connections to internal IP ranges and cloud metadata endpoints. These network controls limit SSRF impact even when application-layer defenses fail. Extended detection and response platforms correlate network anomalies with application behavior to identify SSRF exploitation attempts.
DNS resolution controls add another defensive layer by preventing applications from resolving internal hostnames or private IP addresses. Implementing split-horizon DNS or using dedicated resolvers for external lookups prevents DNS rebinding attacks. Some organizations deploy DNS firewalls that block resolution of metadata service addresses and internal domains from application servers.
Response validation ensures that even successful SSRF attempts don't return sensitive data to attackers. Applications should inspect response content, headers, and status codes before returning data to users. Responses from internal IP ranges or containing specific patterns (like AWS credentials) should trigger security alerts. This approach proves particularly effective against blind SSRF vulnerabilities where attackers rely on application responses for confirmation.
SSRF prevention checklist (defender view)
Effective SSRF defense requires layered controls across application, network, and cloud identity layers.
Core prevention measures include:
- Allowlisting outbound destinations instead of filtering by blacklist
- Blocking access to cloud metadata endpoints at the network layer
- Enforcing IMDSv2 or required metadata headers
- Monitoring for anomalous server-initiated internal requests
- Applying least-privilege permissions to service identities
No single control is sufficient on its own, SSRF prevention depends on reducing both exposure and blast radius.
SSRF detection playbook
Security operations centers need structured playbooks for SSRF detection and response. Detection begins with identifying anomalous server-initiated connections through network monitoring and log analysis. Key indicators include connections to internal IP ranges, metadata service endpoints, or unusual protocols from application servers.
Application logs provide crucial forensic evidence for SSRF investigations. Security teams should monitor for URL parameters containing internal IPs, encoded addresses, or metadata service references. Web application firewalls (WAFs) can flag suspicious patterns, though sophisticated attacks often bypass signature-based detection. Behavioral analysis proves more effective, identifying deviations from normal application communication patterns.
Cloud-native detection leverages platform-specific services like AWS CloudTrail, Azure Monitor, or GCP Cloud Logging. These services can alert on metadata service access, unusual IAM credential usage, or API calls from unexpected sources. Correlation between application logs and cloud audit trails often reveals SSRF attack chains that individual log sources might miss.
Incident response procedures must account for SSRF's potential to compromise cloud credentials and internal services. Upon detecting SSRF exploitation, teams should immediately rotate potentially exposed credentials, review access logs for lateral movement indicators, and assess the scope of internal service access. The average 4-8 week recovery period for SSRF-initiated breaches reflects the complexity of determining attack scope and ensuring complete remediation.
Prevention best practices
Modern SSRF prevention requires architectural decisions that minimize attack surface while maintaining functionality. Service mesh architectures with explicit egress policies provide granular control over service-to-service communication. These architectures make unauthorized connections immediately visible and can automatically block suspicious traffic patterns.
Secure proxy services offer a practical solution for applications requiring URL fetching functionality. Instead of direct server-side requests, applications route through hardened proxies that implement strict validation, rate limiting, and response filtering. These proxies can maintain allowlists of approved external services while blocking all internal network access. This architectural pattern significantly reduces SSRF risk while preserving application functionality.
IMDSv2 adoption remains critical for AWS environments, but organizations should implement additional controls regardless of IMDS version. Network policies blocking metadata service access from application subnets provide defense-in-depth. IAM instance profiles should follow least-privilege principles, limiting damage from successful SSRF attacks. Regular credential rotation reduces the window of opportunity for stolen credentials.
Zero-trust principles apply directly to SSRF prevention — never trust user input, always verify request destinations, and assume breach when designing controls. Modern applications should implement request signing, mutual TLS for service communication, and comprehensive audit logging. These controls complicate SSRF exploitation while providing forensic capabilities when prevention fails.
SSRF compliance and frameworks
Regulatory frameworks and security standards increasingly recognize SSRF as a critical vulnerability requiring specific controls and assessment procedures. Organizations must understand how SSRF maps to compliance requirements and implement appropriate governance structures.
The OWASP Top 10 2021 inclusion of SSRF at position A10 establishes it as a baseline security control for web applications. This recognition means that security assessments, penetration tests, and code reviews must specifically address SSRF vulnerabilities. Organizations following OWASP guidelines must implement the prevention techniques outlined in their comprehensive documentation and regularly test for SSRF vulnerabilities.
MITRE ATT&CK framework maps SSRF to multiple techniques, providing detection and threat hunting guidance. Technique T1190 (Exploit Public-Facing Application) covers initial access through SSRF vulnerabilities, while T1552.005 (Cloud Instance Metadata API) specifically addresses metadata service exploitation. These mappings help security teams align SSRF defenses with broader threat detection strategies and understand attacker tradecraft.
CWE-918 formally classifies SSRF in the Common Weakness Enumeration, providing a standardized reference for vulnerability management systems. CAPEC-664 details the attack pattern, helping security professionals understand exploitation techniques and develop appropriate countermeasures. These classifications ensure consistent vulnerability reporting and facilitate knowledge sharing across the security community. Compliance solutions increasingly incorporate SSRF-specific controls to meet regulatory requirements.
Modern approaches to SSRF security
The evolution of SSRF attacks demands equally sophisticated defensive strategies. Organizations are moving beyond traditional signature-based detection to embrace behavioral analysis, machine learning, and automated response capabilities that can match the speed and sophistication of modern attacks.
AI-powered behavioral analysis represents a paradigm shift in SSRF detection. Instead of relying on known attack patterns, these systems establish baselines of normal server-side request behavior and flag anomalies. Machine learning models can identify subtle indicators of SSRF exploitation, such as unusual request sequences, abnormal timing patterns, or connections to previously unobserved internal endpoints. The 452% increase in SSRF attacks has made manual analysis impossible at scale, driving adoption of automated detection systems.
Zero-trust architectures provide structural defenses against SSRF by eliminating implicit trust between services. Every request requires authentication and authorization, regardless of network origin. Microsegmentation ensures that even successful SSRF attacks have limited blast radius. Service mesh implementations like Istio or Consul enforce these principles at the network layer, making unauthorized connections immediately visible and automatically blocked.
Future trends point toward proactive SSRF prevention through secure-by-default frameworks and infrastructure-as-code practices. Cloud providers are introducing new metadata service protections, including mandatory authentication and network-level controls. Application frameworks increasingly include built-in SSRF protections, making secure URL handling the default rather than an additional security layer.
How Vectra AI thinks about SSRF detection
Vectra AI approaches SSRF detection through the lens of Attack Signal Intelligence™, focusing on behavioral indicators rather than signature matching. The Vectra AI Platform correlates network traffic patterns, cloud audit logs, and application behaviors to identify SSRF exploitation in real-time. By understanding normal communication patterns between services, the platform can detect anomalous server-initiated connections indicative of SSRF attacks, even when attackers use sophisticated evasion techniques. This behavioral approach proves particularly effective against zero-day SSRF vulnerabilities where traditional signatures don't exist.
Conclusion
The dramatic 452% surge in SSRF attacks between 2023 and 2024 marks a turning point in the threat landscape, driven by AI-powered automation and sophisticated threat actors like Cl0p expanding their tactics beyond traditional ransomware deployment. As organizations scramble to meet CISA's October 27, 2025 deadline for patching Oracle EBS, the broader lesson is clear: SSRF has evolved from an obscure vulnerability to a critical threat requiring immediate attention and comprehensive defensive strategies.
The convergence of cloud adoption, microservices architectures, and API-driven development has created an environment where SSRF vulnerabilities can provide direct paths to complete infrastructure compromise. Cloud metadata services, designed for convenience and functionality, have become high-value targets that attackers exploit through increasingly sophisticated techniques. The incidents involving Oracle EBS, Azure OpenAI, and numerous other platforms demonstrate that no organization is immune to SSRF risks.
Moving forward, security teams must embrace a multi-layered approach that combines preventive controls, detection capabilities, and incident response readiness. The adoption of IMDSv2, implementation of zero-trust architectures, and deployment of behavioral analysis tools represent necessary investments in SSRF defense. As AI continues to lower the barrier for SSRF exploitation, defenders must equally embrace advanced technologies to maintain security parity.
For organizations seeking to strengthen their SSRF defenses, the path forward requires both immediate tactical actions and long-term strategic changes. Patch critical vulnerabilities, implement network segmentation, adopt cloud-native security controls, and ensure your security operations can detect and respond to SSRF attacks. The question isn't whether your organization will face SSRF attempts, but whether you'll be prepared when they arrive.
More cybersecurity fundamentals
FAQs
What makes SSRF different from other web vulnerabilities?
SSRF uniquely exploits the trust relationship between servers and internal resources, turning legitimate server functionality into an attack vector. Unlike cross-site scripting (XSS) or SQL injection that target application logic directly, SSRF manipulates servers into becoming unwitting accomplices in attacks against internal infrastructure. The vulnerability's power lies in bypassing network segmentation and firewall rules that would block direct external attacks. SSRF can access cloud metadata services, internal APIs, and backend systems that are invisible and inaccessible from the internet. This server-side nature means that client-side protections like content security policies or browser sandboxing provide no defense. The attack surface extends beyond the vulnerable application to encompass the entire internal network and cloud infrastructure accessible from the compromised server.
Can SSRF attacks be completely prevented?
Complete SSRF prevention remains challenging due to the legitimate need for server-side URL fetching in modern applications. However, implementing defense-in-depth strategies can reduce risk to acceptable levels. Organizations should combine multiple controls including strict input validation with URL allowlisting, network segmentation to limit internal access, metadata service protections like IMDSv2, and behavioral monitoring for anomaly detection. The goal isn't perfection but rather making SSRF exploitation so difficult and detectable that attackers move to easier targets. Regular security assessments, automated vulnerability scanning, and red team exercises help identify gaps in SSRF defenses. Organizations must also maintain incident response capabilities to quickly detect and remediate SSRF attempts that bypass preventive controls.
Why are cloud environments particularly vulnerable to SSRF?
Cloud environments face elevated SSRF risks due to their fundamental reliance on metadata services for instance configuration and credential management. These services, accessible at predictable addresses like 169.254.169.254, provide IAM credentials, API keys, and configuration data that enable cloud resources to function. A successful SSRF attack can retrieve these credentials, granting attackers the same permissions as the compromised instance. The dynamic nature of cloud infrastructure means that traditional network controls often prove inadequate. Auto-scaling, containerization, and serverless architectures create ephemeral resources with varying network contexts. Cloud-native applications extensively use APIs and microservices, increasing the number of components that might contain SSRF vulnerabilities. The shared responsibility model also creates confusion about who should implement SSRF protections, leading to gaps in security coverage.
How can organizations detect active SSRF exploitation?
Detecting active SSRF exploitation requires comprehensive monitoring across multiple data sources. Network traffic analysis should flag unusual outbound connections from application servers, particularly to internal IP ranges, cloud metadata endpoints, or uncommon ports. Application logs might show URL parameters containing encoded IP addresses, localhost references, or metadata service URLs. Cloud audit logs reveal unusual API calls, credential usage from unexpected sources, or metadata service access patterns. Security teams should implement detection rules for DNS queries to internal domains from application servers, sudden changes in server network behavior, and responses containing credential patterns or internal service data. Correlation between these indicators often reveals SSRF attack chains that individual signals might miss. Automated detection systems using machine learning can identify subtle patterns that human analysts might overlook.
What immediate steps should be taken after discovering SSRF?
Upon discovering SSRF vulnerabilities or active exploitation, organizations must act swiftly to contain potential damage. First, implement emergency network controls to block the vulnerable application's access to internal resources and metadata services. Immediately rotate all credentials potentially accessible through the SSRF vulnerability, including cloud IAM credentials, API keys, and service account tokens. Review access logs to identify what internal resources the attacker may have accessed and look for indicators of lateral movement or data exfiltration. Deploy virtual patches through WAF rules while developing permanent fixes. Conduct forensic analysis to understand the full scope of compromise, as SSRF often serves as initial access for broader attacks. Notify relevant stakeholders including security teams, compliance officers, and potentially affected customers if data exposure occurred.
How do SSRF attacks bypass URL validation?
Attackers employ numerous techniques to bypass URL validation controls. URL encoding obscures malicious destinations — %31%32%37%2e%30%2e%30%2e%31 decodes to 127.0.0.1 but might pass filters checking for localhost. Alternative IP representations like decimal (2130706433 for 127.0.0.1) or hexadecimal (0x7f000001) can evade pattern matching. DNS rebinding attacks use domains that initially resolve to legitimate IPs but later change to internal addresses. Parser differential attacks exploit inconsistencies between validation and execution contexts — http://expected.com@evil.com might validate the first domain but connect to the second. Protocol confusion using lesser-known schemes like gopher:// or dict:// can bypass HTTP-only filters. Attackers also chain multiple vulnerabilities, using SSRF to reach internal services with additional vulnerabilities. These evasion techniques highlight why allowlisting remains superior to blacklisting for URL validation.
What role does SSRF play in ransomware attacks?
SSRF has emerged as a critical initial access vector for ransomware operations, as demonstrated by Cl0p's exploitation of Oracle EBS CVE-2025-61882. Ransomware groups use SSRF to steal cloud credentials, enabling them to access and exfiltrate sensitive data before deploying encryption payloads. The vulnerability provides stealthy reconnaissance capabilities, allowing attackers to map internal networks and identify high-value targets without triggering traditional perimeter defenses. SSRF access to cloud metadata services can grant permissions to delete backups, modify security configurations, or disable logging — actions that maximize ransom pressure. The shift from traditional phishing-based initial access to SSRF exploitation represents a tactical evolution among ransomware operators. This trend particularly threatens organizations with internet-facing applications, as SSRF vulnerabilities can be identified and exploited through automated scanning.
Does SSRF lead to cloud metadata exploitation?
Yes. SSRF is one of the most common ways attackers access cloud metadata services. When a vulnerable server can be coerced into making internal requests, attackers can retrieve credentials, tokens, and configuration data from metadata endpoints that are not directly accessible from the internet. This allows SSRF to escalate from a web vulnerability into full cloud account compromise.
Why is SSRF more dangerous than other web vulnerabilities?
SSRF is especially dangerous because it abuses trusted server identity rather than user interaction. Unlike vulnerabilities that expose a single application, SSRF allows attackers to pivot into internal networks, cloud control planes, and metadata services. This makes SSRF a gateway vulnerability that often enables privilege escalation, lateral movement, and ransomware deployment.
Is SSRF typically an initial access or post-compromise technique?
SSRF is most often used as an initial access technique that enables deeper compromise. Attackers exploit SSRF to gather internal intelligence, steal cloud credentials, and map internal services. Once access is established, SSRF is frequently chained with lateral movement, credential abuse, or ransomware deployment.